The goal is to create a USB key that contains a Linux based operating system. Any Linux compatible computer can then be booted with this USB key, temporarily borrowing the host computer. The hosted Linux OS can then access an encrypted partition that houses important private information that may be helpful in an emergency. This technique offers the maximum portability of accessible, private information such as your will, financial data, credentials, etc.
I previously had an USB key formatted with an encrypted Mac filesystem storing the same information. However, this is inconvenient because you will need to find a Mac in an emergency situation.
In the Linux community, you can create a Live USB key. The concept is to create an operating system that will run off of the USB key with any computer that you can plug the USB key to. However, many of these Live USB distributions does not remember any changes that you make while using the operating system. The next time you boot from the Live key, all your previous changes are gone, and the Linux environment reverts back to its original, pristine state. To remember the changes during uses, these changes have to be “persisted”.
I started to find the best methodology for creating a Live Linux USB that operates with an encrypted persistent partition.
All the commands in this article has been performed within the Ubuntu 18.04 LTS Desktop install. I installed this version on both VirtualBox and Parallels on the Mac. Both worked beautifully but Parallels has smoother integration with Mac.
I tried first the Kali distribution, using the instructions in this USB Persistence & Encrypted Persistence article (Article 1). However, the USB stick that I was using which was a Kingston DTSE9 G2 USB 3.0 32GB, was simply way too slow on writes causing the Live USB almost unusable.
I searched for an alternative USB stick and settled for the SanDisk 64GB Ultra Fit USB 3.1 Flash Drive. This new USB stick’s write performance was 4x faster than the Kingston.
After learning more about initramfs hooks, boot loaders, and a refresher on UEFI and BIOS booting process and partition layout strategies for USB storage devices, I decided to roll my own Live USB using the Ubuntu Desktop as a base along with the mkusb tool for the initial layout. The reason for the change is that I already have Ubuntu else where in the house so standardization is probably a better bet.
To improve performance further, I decided that it is not necessary to encrypt the persistent partition where the system configuration updates will be stored. Instead, I will create my own private encrypted partition to store only the private data that requires protection. Article 1, also provided details on how to use the LUKS technology to encrypt any Linux partition, so my exercise with Kali Linux was not a total waste of time.
Before I run mkusb, I needed to install it first by doing the following:
sudo add-apt-repository universe sudo add-apt-repository ppa:mkusb/ppa sudo apt-get update sudo apt-get install mkusb mkusb-nox usb-pack-efi
I ran the mkusb tool (after sudo su - )1, with the following options:
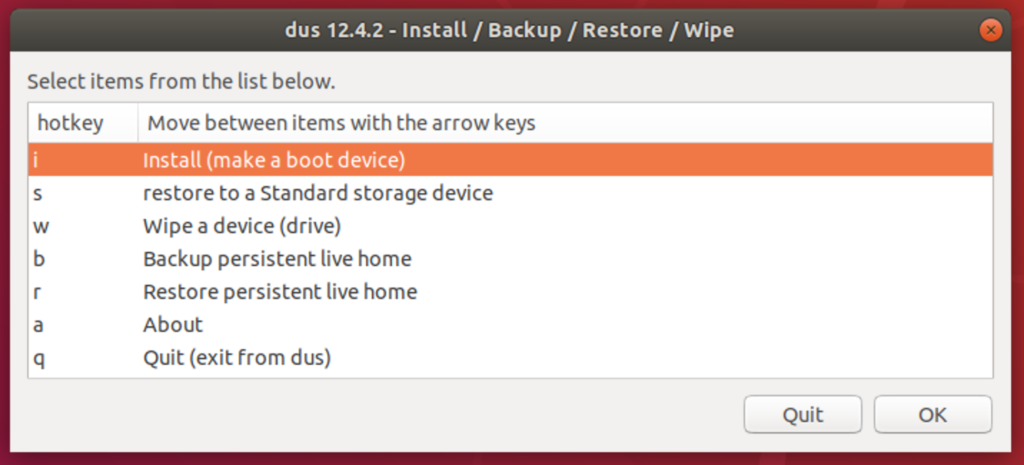
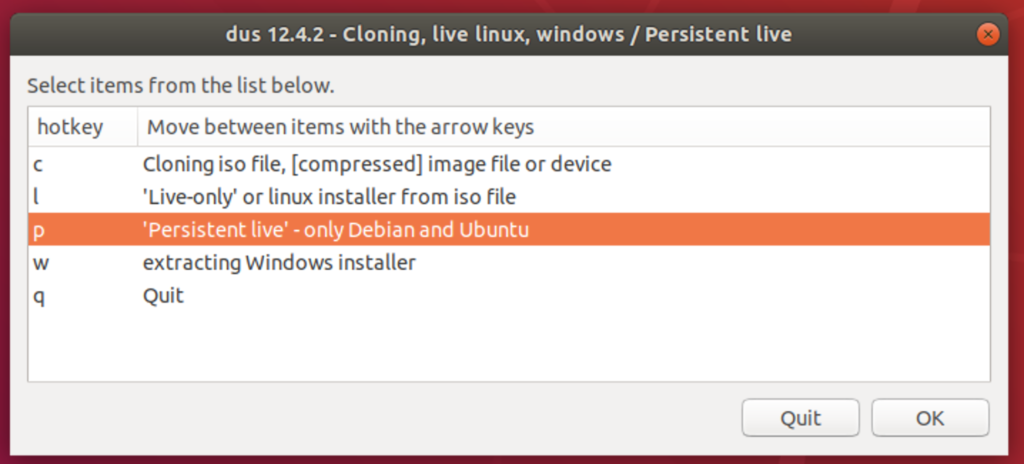
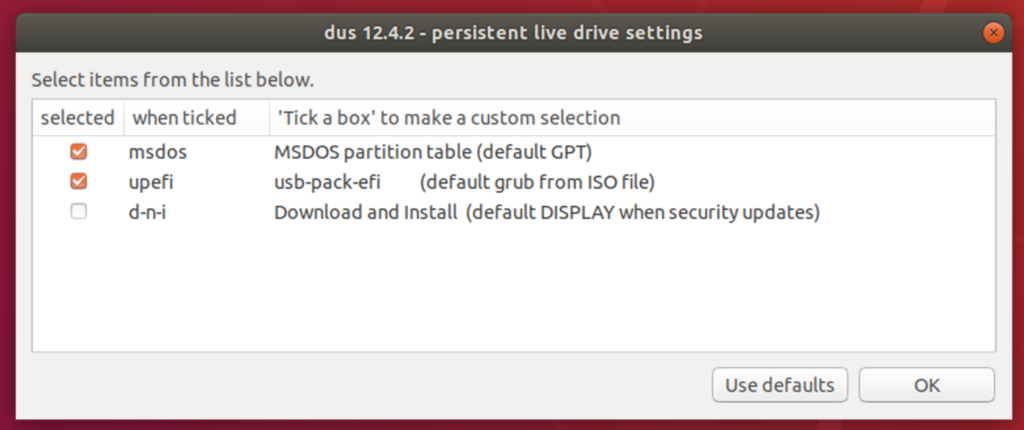
We also chose msdos so that more computers will be compatible for booting. Once mkusb is completed, we will need to perform some custom partition layout. We will use the gparted program for this purpose so that the completed partition layout will look something like this:
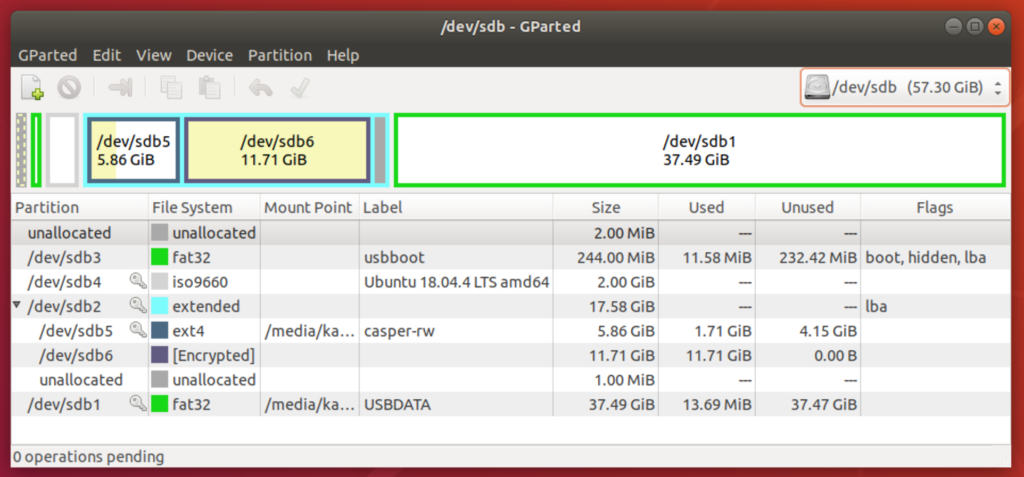
We first deleted the original usbdata partition and grew the extended partition (/dev/sdb2) to about 18 GB, approximately 6 GB for casper-rw, which the system will store any custom configurations or upgrades since this Live USB key is created. We create another logical partition called Personal that is around 12 GB in size, which will be encrypted and this is where we will store private, sensitive data for emergency use.
The remaining space will be allocated to USBDATA, a last primary partition for normal USB data sharing, the typical use case for a USB stick. We also want to make sure that the other FAT32 (usbboot) partition is not visible in Windows by setting the hidden partition flag. We did that with the gparted program as well.
Once the partition table is completed, we can now encrypt the Personal (/dev/sdb6) partition. For this, we went back to Article 1, which gave us the following instructions.
~# cryptsetup --verbose --verify-passphrase luksFormat /dev/sdb6
WARNING!
This will overwrite data on /dev/sdb6 irrevocably.
Are you sure? (Type uppercase yes): YES
Enter passphrase for /dev/sdb6:
Verify passphrase:
Key slot 0 created.
Command successful.
~# cryptsetup luksOpen /dev/sdb6 myusb
Enter passphrase for /dev/sdb6:
~# mkfs.ext4 -L Personal /dev/mapper/myusb
~# cryptsetup luksClose /dev/mapper/myusbAll Done! Now we have a bootable USB stick that can be booted from any Ubuntu compatible computer. I can store my own personal data in a very safe and private way within the encrypted Personal partition, while any changes I make to the system will be preserved in between the uses of the USB stick. On top of it all, the USB still has 40+ GB (~37.5 GiB) of storage for normal USB transfer usage.
I spent sometime copying some confidential information which I think I will need in an emergency into the Personal partition. I want to duplicate the finished Live USB key, so that both my wife and I will have a copy always available to us on our physical keychain.
I did this on my Mac, and the command to duplicate the USB drive is:
sudo dd if=/dev/rdisk2 of=/dev/rdisk3 bs=4m conv=notrunc
If the USB key ended up to be lost, then whoever picks it up will need to:
- Recognize that this is a bootable USB, otherwise it will just seem like 40GB USB Flash Drive;
- Get the password needed to login to Linux; I thought about installing two factor authentication but decided not to, because any good hacker can simply access the partition from another Live Key;
- If they do mount the partition manually, then they still need to obtain the LUKS key to decrypt the partition; I made the LUKS key to be different than the OS password and is twice as long.
I think the risk is worth the benefit of having critical info around in case of an emergency.
Update: WiFi on MacBooks
It looks like MacBooks uses Broadcom WiFi chips and most Linux distributions do not ship with these drivers. This can be easily solved by loading the following software:
sudo apt update
sudo apt install bcmwl-kernel-sourceEven with the above software installed, there is still a little ritual:
- Launch the “Software and Updates” application;
- Select the “Additional Drivers” tab;
- Select “do not use this driver” and allow the process to go through and reboot the system;
- Re-enter the system and repeat steps 1 & 2, and then select the Broadcom drivers;
- Without rebooting, WiFi networks should be available for use
Unfortunately the above ritual will have to be performed every time the Live USB stick is powered off.
Update: Tried Linux Live Kit
I wanted to further customize my Live USB key. Instead of keeping a persistent partition, I thought I would keep a Linux VM at home and ensure that it is up to date and customized. At certain intervals, I would then create a Live USB key from the VM install.
I tried Linux Live Kit, but the results were disappointing. I was able to create a bootable USB key that worked, but the OS did not recognize the MacBook’s keyboard or trackpad. For some reasons, the drivers required did not get bundled during the process. I’ll have to read up on how I can create a Live USB key from scratch rather than depending on these tools, but it is more complicated than I thought, so for now this idea will have to be shelved until I have more time.
1For some reason mkusb will not work with the live persistence if I simply do a sudo mkusb or under a non-root account. The only way that I can get it to work is to run it within a root login session.
