All of this started with one of my neighbour whose laptop broke down. The laptop stopped recognizing its internal SATA connection, so it will not boot. My neighbour ended up booting Windows from an external SSD using a Windows to Go solution to continue to use his laptop.

This somehow got me thinking whether it is possible to boot Windows from an external SSD using a Mac. I knew Bootcamp allows you to create a dual boot scenario on the Mac, but the default procedure requires you to repartition your internal drive space to do so.
With external SSD drives coming down in price, for example you can get a 500GB Samsung T5 now for less than $130 CAD, it would seem a pretty sweet deal to have Windows on the side with your MacBook.
After doing some research, it seems like others have similar ideas. I am not going to detail all the steps, since you can find YouTube videos and other forums that have already done the deed. Instead, the high level process goes something like this:
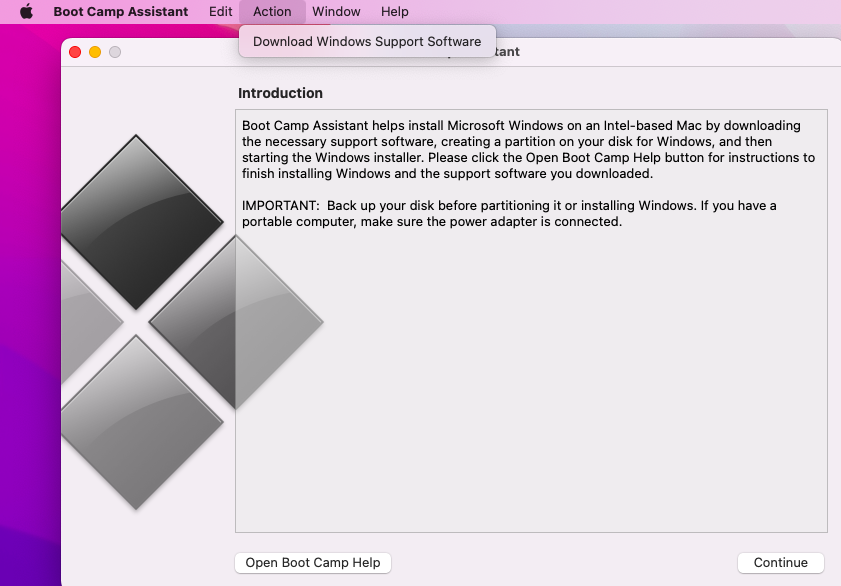
- Use the Bootcamp Assistant App on the Mac to collect all the drivers on a USB stick or a local folder on your Mac. Do not use the wizard. You will need to use the Action menu. See Figure 1 below.
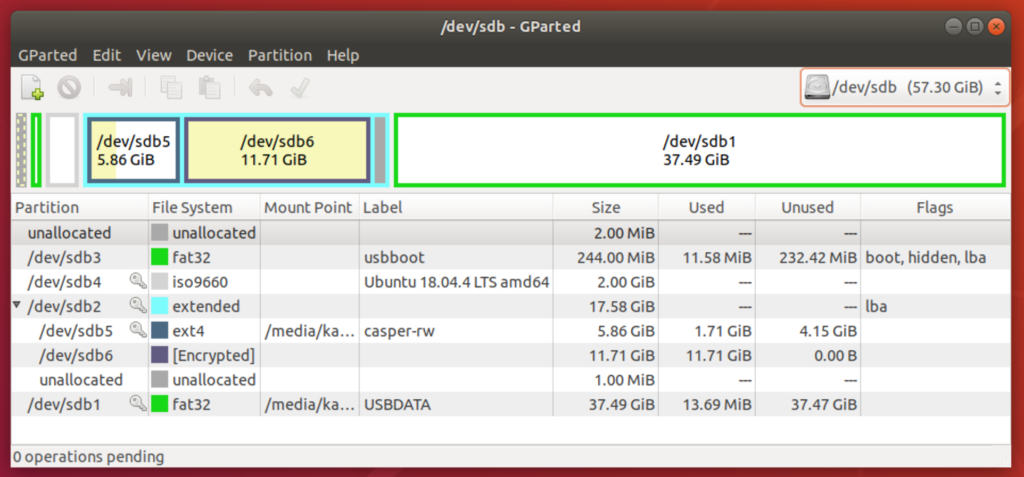
- Download a Windows ISO and use a Virtual Machine (e.g. Parallels, VirtualBox, etc.) to install the Windows ISO onto an external SSD drive. I first tried VirtualBox but ran into Catalina permission issues that I could not circumvent. I ended up doing it with Parallels which I will go into details later.
- Copy the drivers from the USB stick created in 1 into the desktop of the recently installed Windows on the SSD drive.
- Reboot your Mac and hold the option key down before the Apple logo shows and boot into the EFI portion that contains Windows.
- Make sure you have an external keyboard and mouse handy because the default Windows install may not recognize the native hardware yet. On my MacBook Air, I had no issues.
- Once Windows come up, login and run the Bootcamp setup from the desktop that was originally copied from the USB stick.
- Once this is all done, you can dual boot into Windows on the Mac as long as you have that SSD drive handy.
So far everything works, and it is happily installing Visual Studio 2019. I even tried Cortana and the mic and speakers are working well. I did a quick Skype test call and the webcam is working well too.
I do want to document the steps that I performed with Parallels when installing Windows 10 onto the SSD. Those steps were not intuitive.
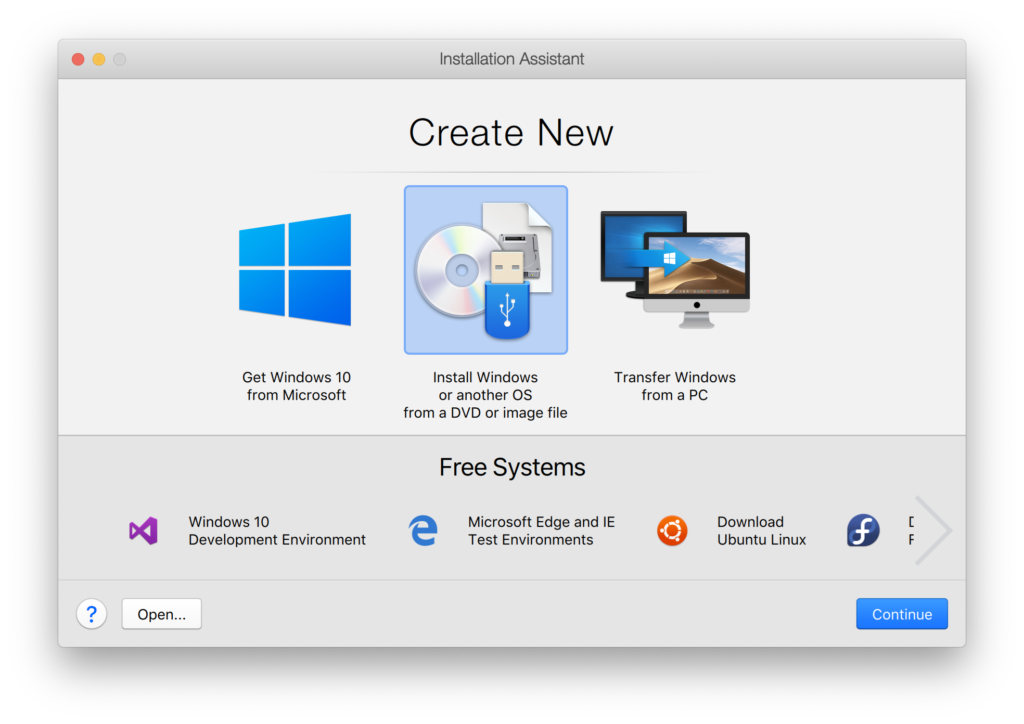
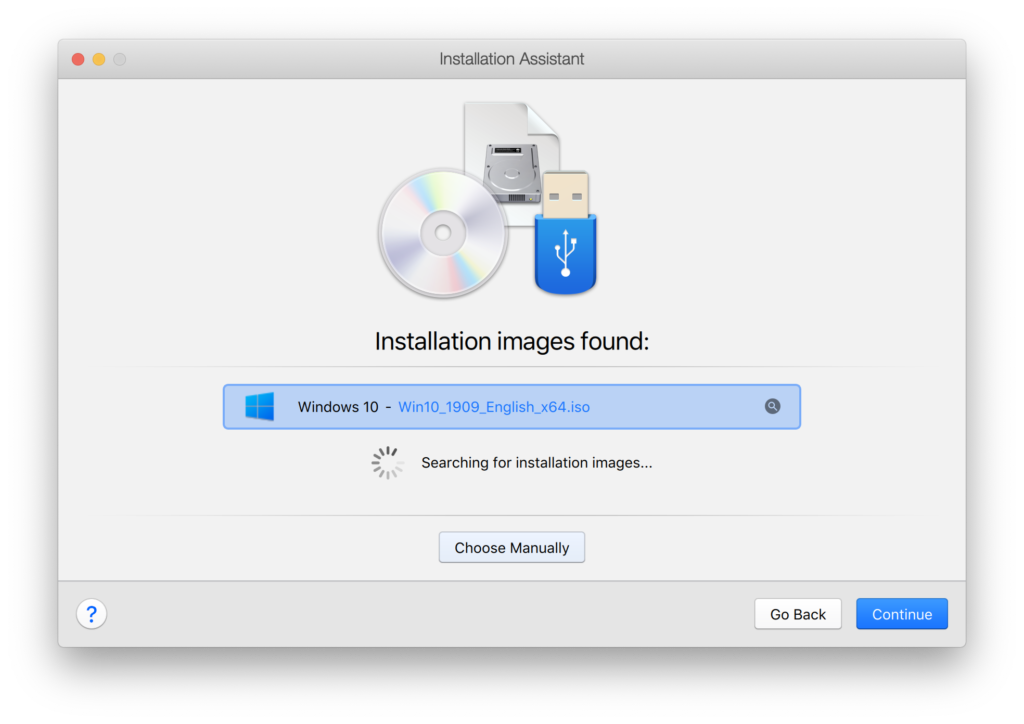
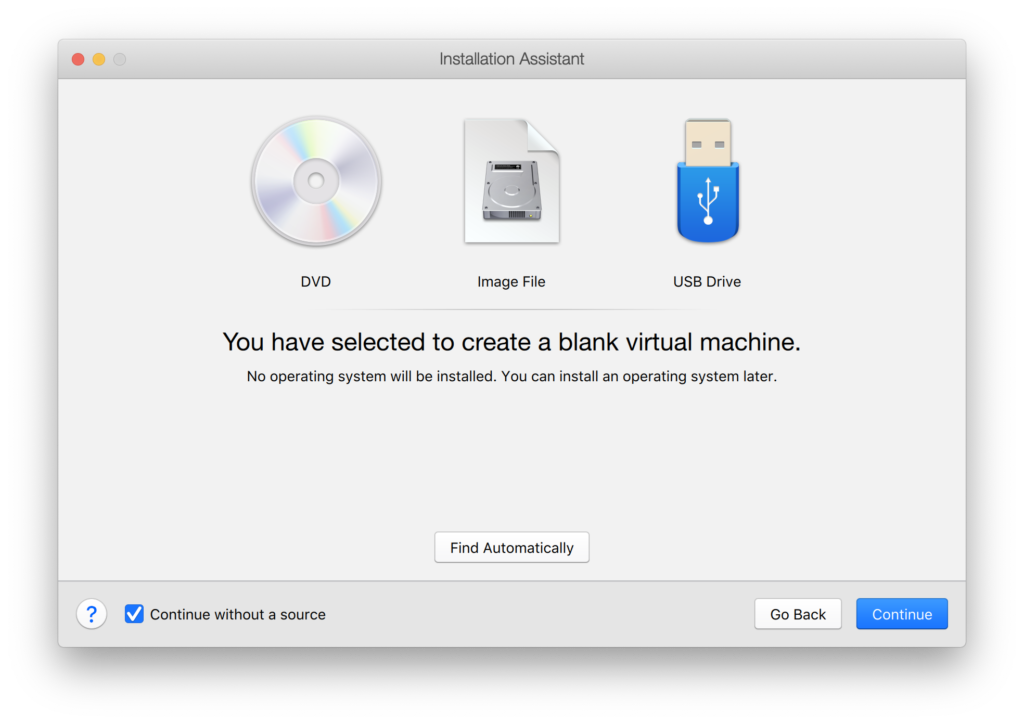
After this, stop the virtual machine and make the following custom configurations:
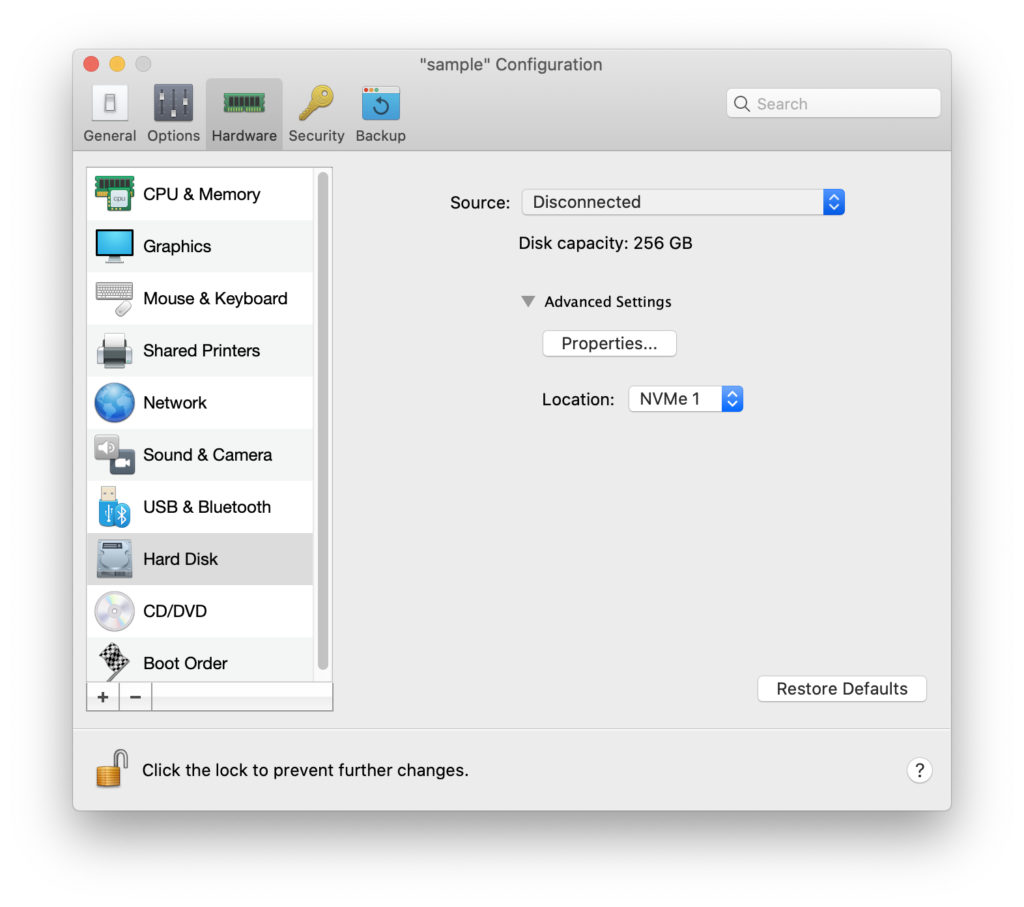
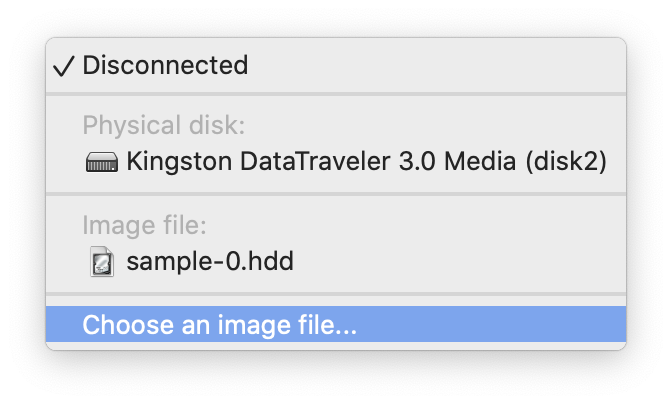
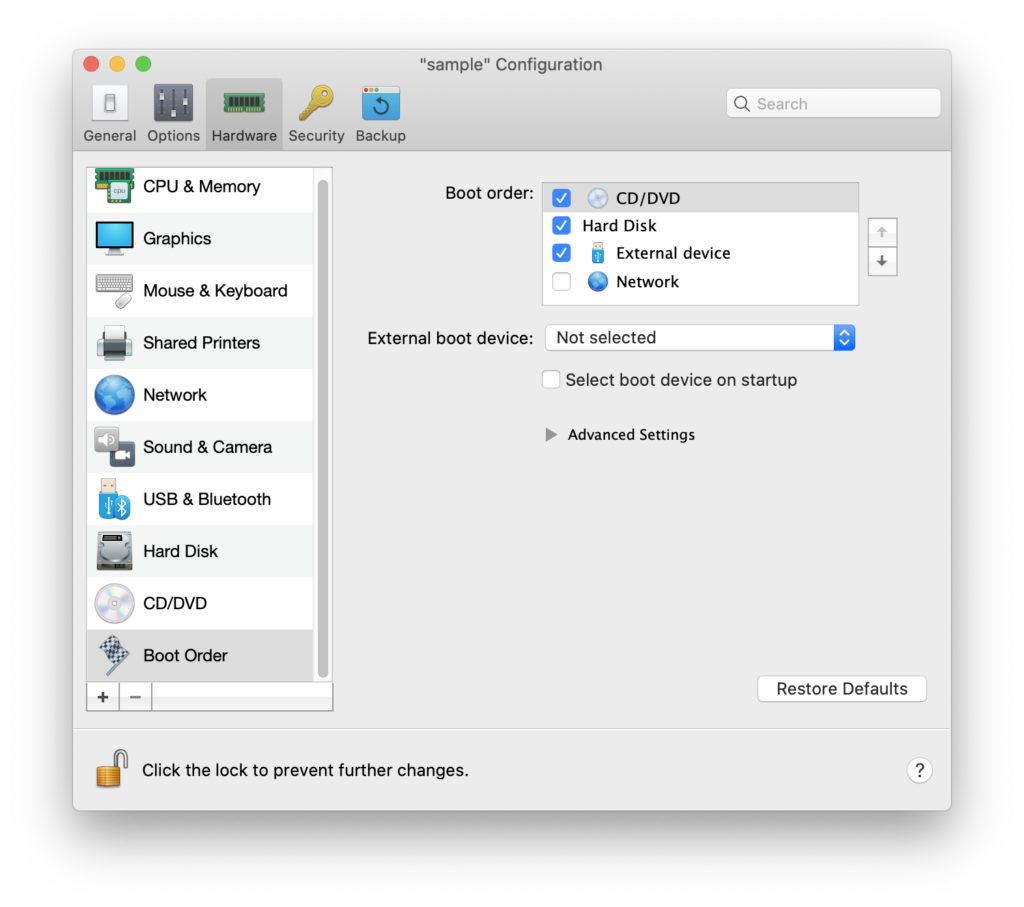
Start the Virtual Machine and it will go through the first part of the Windows installation. Once it is completed, it will reboot. Instead of booting from the external media, it will boot from the CD ISO image again. Simply shutdown the VM again and change the boot order again.
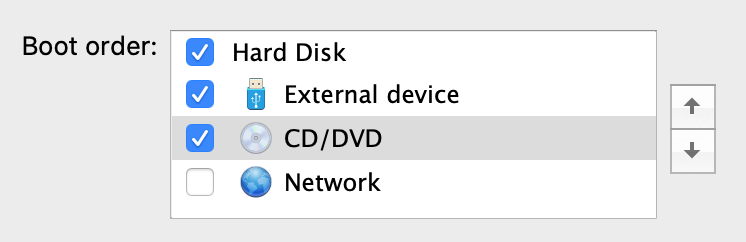
Once Windows 10 complete its installation, it will go through a user account setup process. If you are connected to the Internet during this stage, Windows 10 will force you to either use an existing Microsoft account or create one. This is unfortunate, but go ahead and create a temporary one. Remember to create a local administrator account and remove this temporary Microsoft account as the final step of the Windows setup.
Remember to copy the Bootcamp drivers from the USB stick to the Windows desktop before completing and shutting down the virtual machine.
Now you are ready to restart the Mac and dual boot into the external drive by holding the Option key while the machine restarts. The final step is run the Bootcamp Setup.exe program, which should be located inside the Bootcamp folder that your previously copied on the desktop. This is the last step of the Windows configuration on the SSD drive, and you can restart your Mac and dual boot into Windows one final time.
You are now running Windows natively to the Mac’s metal, without any simulators or Virtual Machines. This process is great to revitalize old MacBook’s lying around especially for students who need a Windows computer for their curriculum, but still want to retain their macOS. For more contemporary Mac’s, the small form factor and the speed of the Samsung T5 drive is a great fit for this type of situation. This is very cool!
Update: Potential Trouble with Major Windows Update
I have been told that a major Windows Update could encounter an error and a registry setting is required to fix this. The following page has more information on this. In summary, you have to set the following registry key PortableOperatingSystem from 1 to 0. This key can be found at registry location HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control. Thanks to Martin Little for this very helpful information.
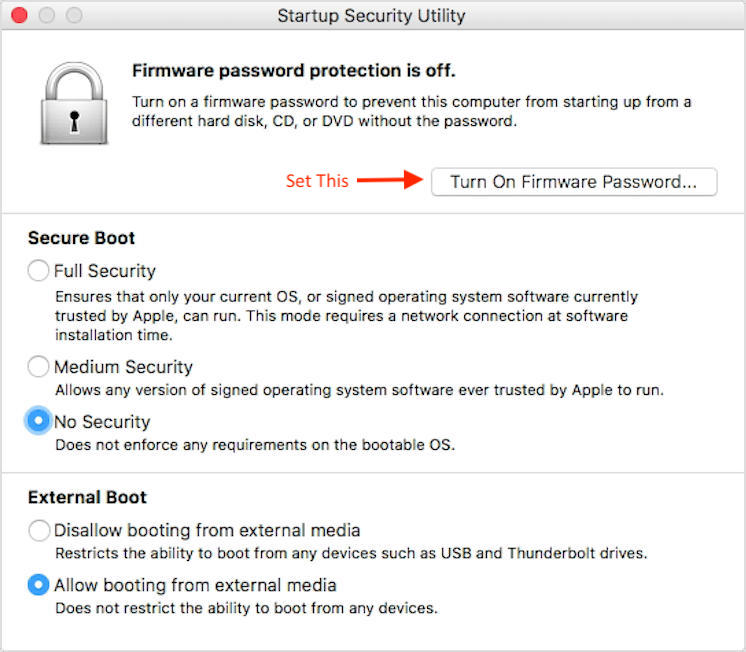
Update: Mac’s with Secure Boot using the T2 Chip
To allow a Mac with the T2 chip to boot from an external drive certain settings have to be made with the Startup Security Utility. This utility can be accessed via the Mac’s recovery mode, under the Utilities menu. You want to disable secure boot and allow for external drive. Since the secure boot is disabled, set a firmware password to prevent a bad actor booting their own operating system with their own Live USB key.